Secure by Design: Embedding Continuous Security in AWS Pipelines
Explore how Continuous Security on AWS transforms security into an integral part of CI/CD pipelines, ensuring automated, scalable, and proactive defenses throughout the software delivery lifecycle.

In my past posts, I’ve written about strategies for building and scaling businesses on AWS. From fostering a remote-first culture to leveraging the Amazon PR/FAQ process and developing systems like the AWS Partner Flywheel, the focus has often been on business outcomes.
Today, I’d like to shift gears to focus on the technology that drives secure and scalable systems on AWS—specifically, Continuous Security on AWS. This model ensures that security isn’t relegated to a periodic task performed by downstream teams but is instead embedded directly into deployment pipelines as part of your organization’s DNA.
By aligning with the AWS Deployment Pipeline Reference Architecture (DPRA), organizations can embrace automation, integrate security into the CI/CD process, and ensure robust security mechanisms from day one. This post outlines how Continuous Security fits into the DPRA pipeline stages, ensuring that security, like quality, is built in—not bolted on.
Continuous Security: Automate, Pipeline, Secure
Continuous Security on AWS relies on a simple yet transformative mental model: Automate, Pipeline, Secure.
- Automate: Treat all security controls as code, enabling consistent, repeatable, and scalable processes.
- Pipeline: Integrate security directly into CI/CD pipelines to catch issues as early as possible.
- Secure: Safeguard your pipeline and systems through least privilege access, encryption, monitoring, and event-driven responses.
This approach accelerates the speed of delivery while ensuring that security is a continuous, integrated process—not a manual, downstream bottleneck.
Case Study Highlight: National Australia Bank (NAB), a leading Australian financial institution, revolutionized its security operations by leveraging AWS to automate compliance and security defect detection. By integrating AWS-native services into their DevSecOps practices, NAB reduced the time to identify and remediate security gaps from 19 days to just 45 seconds. This innovative approach ensured enterprise-wide security updates automatically, significantly enhancing the bank's ability to proactively manage vulnerabilities and maintain robust security standards.
Aligning Continuous Security with the AWS DPRA
The AWS Deployment Pipeline Reference Architecture (DPRA) provides a structured approach to CI/CD, ensuring software systems are reliable, scalable, and secure. Based on how Amazon operates its own internal deployment processes (as documented in the Amazon Builders' Library), the DPRA outlines best practices for automating deployments at scale.
While the DPRA outlines a comprehensive structure, not all stages are required for every service. For smaller or less complex services, certain stages (e.g., Beta and Gamma) can be combined or streamlined to balance speed and security. Tailoring the pipeline to the service’s size, risk tolerance, and complexity ensures that you meet critical security and validation needs without introducing unnecessary delays.
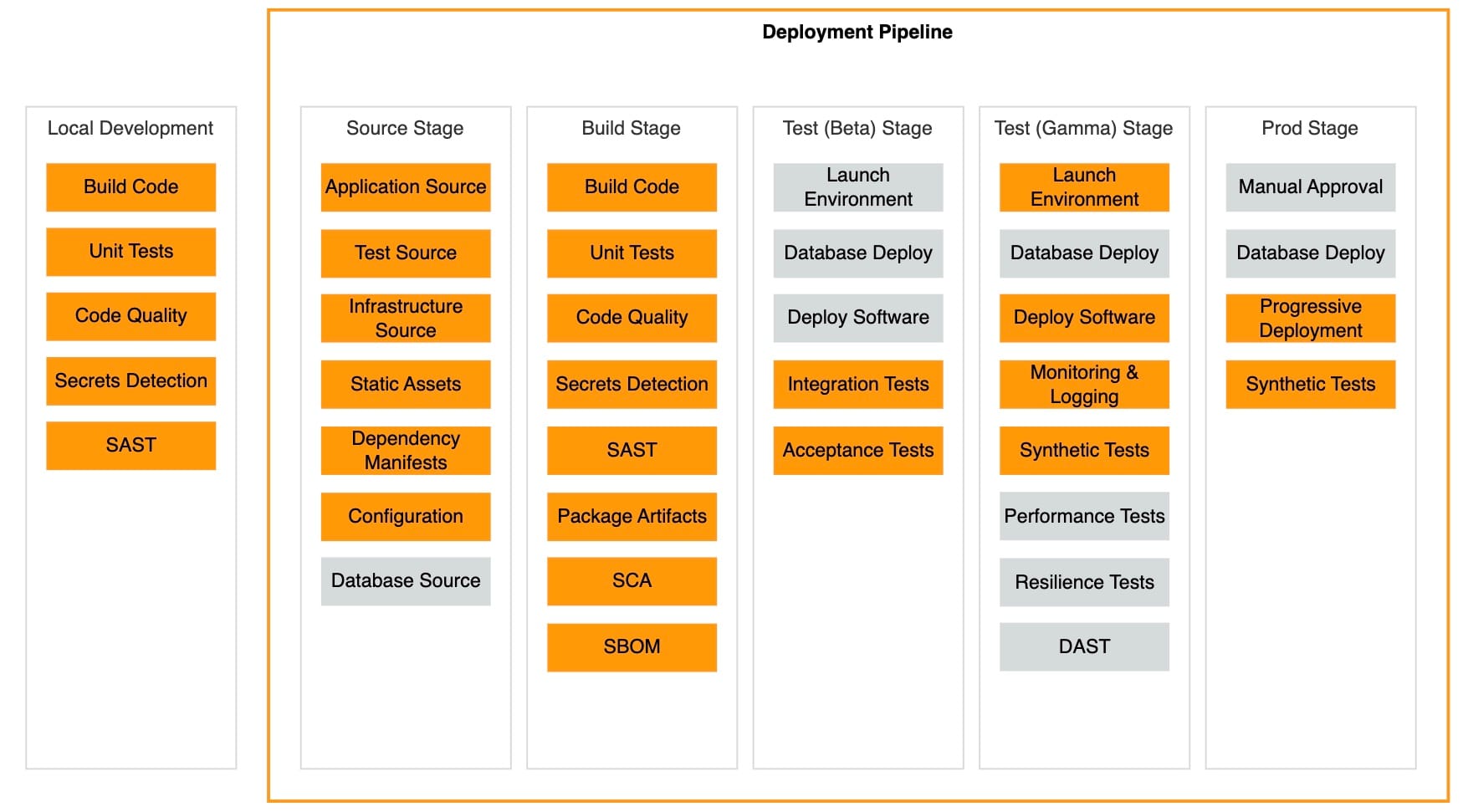
Below is a detailed breakdown of how Continuous Security maps to each DPRA pipeline stage.
1. Source Stage
Purpose: Validate the integrity of your application source code and dependencies.
Key Actions:
- Static Application Security Testing (SAST): Scan source code for vulnerabilities like SQL Injection or Cross-Site Scripting (XSS).
Example tools: Amazon CodeGuru, SonarQube, Checkmarx. - Secrets Detection: Identify hard-coded secrets, such as passwords or access keys.
Example tools: GitGuardian, gitleaks. - Dependency Manifests: Validate dependency files to ensure proper versioning and no known vulnerabilities.
Example tools: Snyk, Dependabot. - Infrastructure Source Validation: Scan IaC templates for misconfigurations.
Example tools: cfn-nag, Checkov. - Governance Controls: Enforce boundaries on source control and artifact storage.
Example tools: SCPs to restrict IAM roles from accessing unauthorized S3 buckets where deployment artifacts are stored; RCPs to ensure artifacts and repositories, such as those integrated with GitHub or GitLab, can only be accessed from secure environments or trusted accounts.
Compliance Tip: Integrate security controls aligned with compliance standards such as ISO 27001, SOC 2, or GDPR from the outset to minimize downstream compliance gaps.
2. Build Stage
Purpose: Compile the application, run unit tests, and generate artifacts for deployment.
Key Actions:
- Unit Testing: Verify functionality at the code level.
Example tools: PyTest, JUnit. - Software Composition Analysis (SCA): Analyze open-source dependencies for vulnerabilities.
Example tools: Snyk, Black Duck. - Software Bill of Materials (SBOM): Generate an inventory of software components to meet compliance needs.
Example tools: CycloneDX. - Secrets Detection: Double-check that no sensitive information is included in build artifacts.
Pro Tip: Use AWS CodeBuild with IAM roles for least-privilege access to ensure secure build operations.
3. Beta Stage (Testing Environment)
Purpose: Deploy the application to a test environment and perform functional and acceptance tests.
Key Actions:
- Launch Environment: Provision infrastructure for testing using IaC tools like AWS CloudFormation or Terraform.
- Acceptance Testing: Validate that the application meets functional requirements.
Example tools: Cucumber. - Monitoring and Logging Validation: Ensure observability is in place.
Example tools: Amazon CloudWatch, Datadog.
Compliance Tip: Enable logging and monitoring aligned with frameworks such as PCI DSS, which requires clear audit trails for test environments.
4. Gamma Stage (Performance and Resilience Testing)
Purpose: Conduct advanced testing for performance, resilience, and runtime vulnerabilities.
Key Actions:
- Synthetic Testing: Simulate user behavior to validate performance and functionality.
Example tools: Amazon CloudWatch Synthetics. - Resilience Testing: Evaluate the system's ability to recover from failures.
Example tools: Gremlin, Chaos Toolkit. - Dynamic Application Security Testing (DAST): Scan for runtime vulnerabilities.
Example tools: OWASP ZAP, StackHawk.
Pro Tip: Integrate AWS Fault Injection Service to assess your system's resilience under failure scenarios.
5. Production Stage
Purpose: Safely deploy the application to production and ensure its security and reliability.
Key Actions:
- Progressive Deployment: Roll out changes incrementally using canary or blue/green deployments.
Example tools: AWS CodeDeploy. - Post-Deployment Monitoring: Use services like Amazon GuardDuty and Amazon Inspector for ongoing security and threat detection.
- Continuous Security Practices: Implement automated, continuous auditing to ensure compliance and proactively manage vulnerabilities:
- Continuous Monitoring: Use Amazon CloudWatch and AWS Security Hub to track security events, compliance drift, and operational anomalies in real-time.
- Automated Remediation: Leverage AWS Lambda and AWS Config Rules to respond automatically to security incidents or non-compliant resources. For example, non-encrypted S3 buckets can be flagged and corrected automatically.
- Continuous Auditing: Establish automated compliance checks with tools like AWS Audit Manager or AWS Config to continuously validate your infrastructure against frameworks like ISO 27001 or PCI DSS.
Example: Use AWS Config Rules to scan for misconfigured resources and generate automated reports on compliance status.
Compliance Tip: By automating compliance checks and remediation, organizations can maintain near-real-time alignment with security standards while reducing manual effort.
Case Study Highlight: DXC Technology, a global IT services leader, developed the Continuous Delivery Express solution to assist clients in implementing DevSecOps CI/CD pipelines. This solution integrates security measures into the development and operational processes, enabling faster and more secure application releases.
Why Continuous Security Matters
Security is no longer a final checkbox in the SDLC. By embedding it into every pipeline stage, Continuous Security enables:
- Faster Feedback: Identify vulnerabilities early, saving time and resources.
- Reduced Risk: Prevent misconfigurations and vulnerabilities from reaching production.
- Speed of Delivery: Automate manual security tasks to remove bottlenecks.
When security is seamlessly integrated into your delivery process, customers benefit from faster feature rollouts, fewer disruptions, and greater confidence in your systems. By prioritizing Continuous Security, you not only protect your organization but also vastly improve the experience for your customers—building a foundation of trust and reliability that sets your business apart.
